We all need to ensure our websites are accessible to legitimate visitors, don’t we? That’s why a DOS (denial of service) or DDOS (distributed denial of service) attack can cause such problems. For those who don’t know, this is when a server is maliciously overloaded with connection requests to render it inaccessible to legitimate visitors.
I recently had a problem with many DOS attacks on my server happening at once, going on for several hours. I don’t suspect that this was a true, large-scale DDOS attack (when multiple, different IPs coordinate the attack), since I still had some SSH-side connectivity and the number of very different IPs was still no more than a handful. That said, the number of new IPs coming in meant that it could no longer be dealt with manually. I needed something to automatically reject and ban suspicious IPs.
After speaking to an old developer friend who manages and hosts several websites on self-managed servers for his clients, it transpired that over all the years, he’d never actually had cause to look into this. This will be one of the other many ‘benefits’ of running a popular blog… My friend didn’t know of any quick solutions and had no time to help me out, either, so I decided to do some research and solve it for myself.
I did some research and came across CSF firewall: a Linux-based firewall that is not too much work to install on a VPS like mine. To install it, I largely followed the instructions at DigitalOcean – it says Ubuntu there, but it obviously works the same way for Debian Wheezy, for example. For the record, DigitalOcean is also the host my friend recommends for good self-managed VPS servers in the UK (I use a different host based in Germany for legal and data security reasons).
It was pretty easy to set up and there is a whole ‘host’ of options you can deploy to plug any holes in your existing security. For example, in a DOS attack, this firewall can be used to automatically ban any IP making more than X connections to a given port. You can also block any ports you know you don’t need to have open, for incoming and/or outgoing connections as required. There are lots of other useful settings, but that should give you an idea to start off with. If you search for “recommended CSF settings”, you’ll find a number of discussions and blog posts with different ideas for different circumstances.
A word of caution, though: CSF comes with a testing mode to minimise the risk of something going wrong, but it is possible to render your server inaccessible. The testing mode protects you in that it clears changes to the IP tables (blocked list) every five minutes, although you can extend this to a longer period if you are trying something especially innovative. I kept it on testing mode for a couple of hours to see what was happening and then made the change permanent.
I am very happy to say that I appear to have fixed the problem. See below for a screenshot of connections to port 80 (HTTP) both before and after the change on an otherwise quiet afternoon.
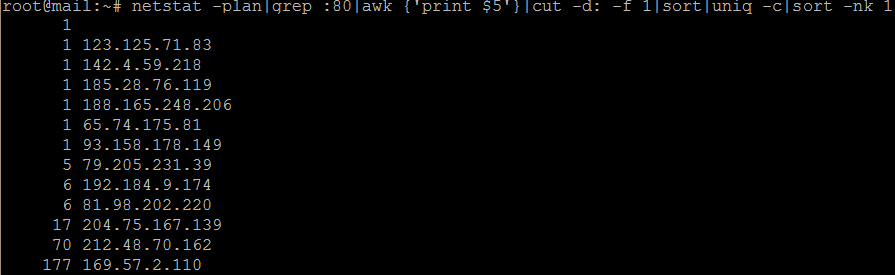
My server before installing CSF firewall, during a DOS attack.
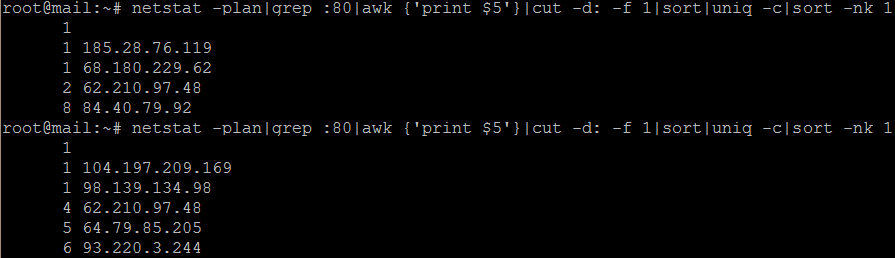
My server after installing CSF firewall, now properly protected against DOS attacks.


That is so far above my head but I am really glad you fixed it. Now I know who to ask if the same happens to me!